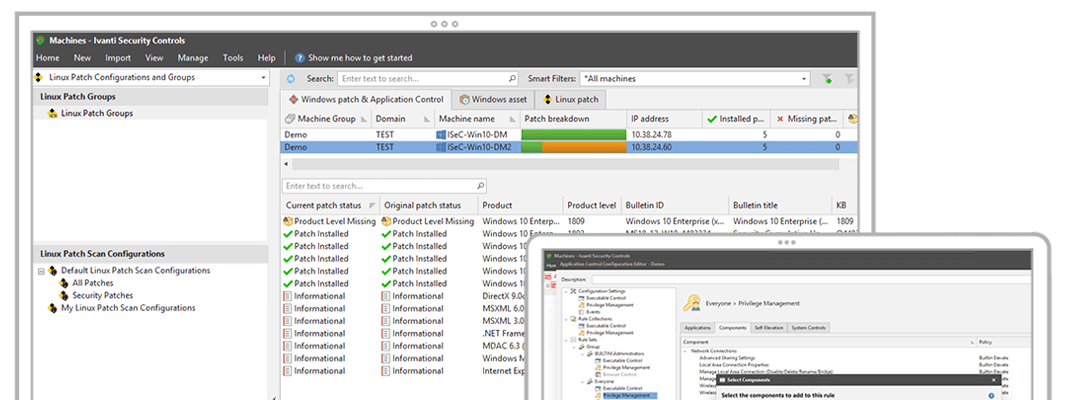
Ivanti Security Controls simplifies security with unified and automated prevention, detection, and response techniques that target your biggest attack vectors. It provides the security global experts agree creates the highest barriers to modern cyber attacks, including discovery, OS and application patch management, privilege management, and allowlisting.
Discovery of vulnerabilities
Scan physical and virtual systems for missing patches.